Posted on February 9, 2025
Quantum Cryptography
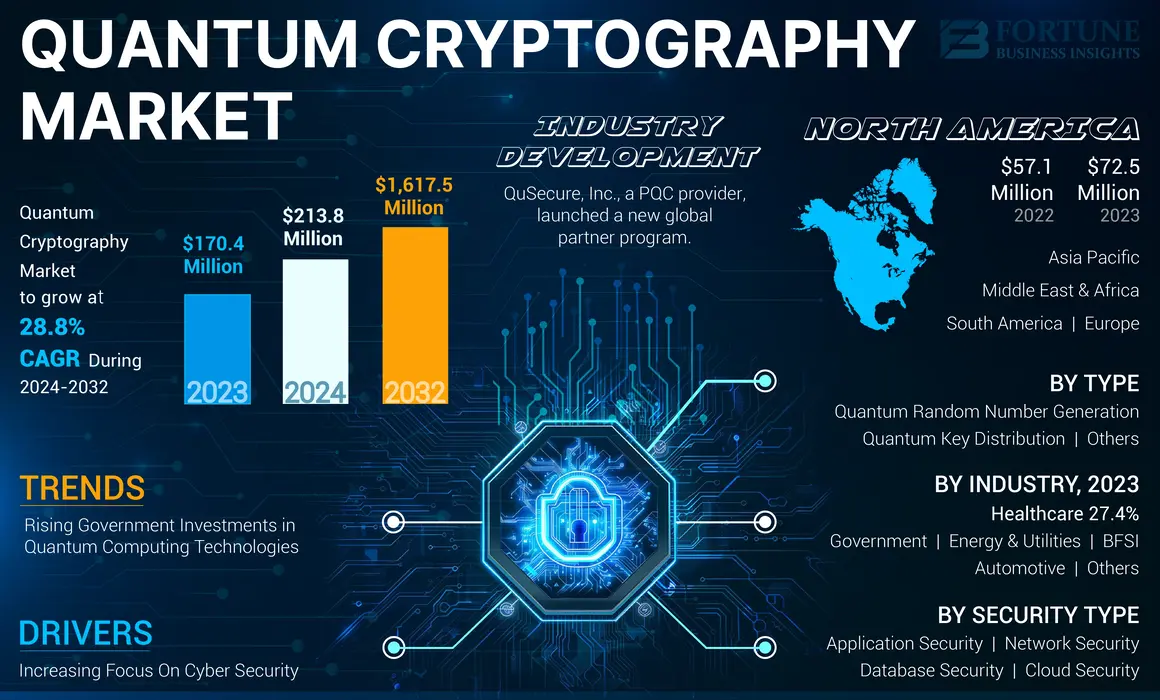
Quantum cryptography leverages the principles of quantum mechanics to achieve security in communication that is theoretically unbreakable by traditional methods, primarily through a method known as Quantum Key Distribution (QKD). Here’s a detailed look at how quantum cryptography works and its implications:
Principles of Quantum Cryptography:
Quantum Superposition:
Particles like photons can exist in multiple states simultaneously (e.g., both vertical and horizontal polarization at once). When measured, they collapse into one state, which is random unless the measurement method is known.
No-Cloning Theorem:
It’s impossible to create an identical copy of an unknown quantum state. This principle ensures that any attempt to intercept or copy the quantum key will introduce detectable errors.
Heisenberg Uncertainty Principle:
You cannot measure one property of a quantum system (like the polarization of a photon) without disturbing another related property, making eavesdropping detectable.
Quantum Key Distribution (QKD):
BB84 Protocol (named after its creators Bennett and Brassard in 1984) is one of the most well-known methods for
QKD:
Steps:
Key Generation:
Alice (sender) sends Bob (receiver) a series of photons, each polarized in one of four states (e.g., vertical, horizontal, diagonal, or anti-diagonal).
Bob measures these photons randomly choosing from the same set of polarization bases.
Sifting:
Alice and Bob communicate over a public channel about which bases they used for each photon. They discard results where the bases didn’t match, leaving a shorter but secure key.
Error Detection:
They compare a subset of their bits to check for errors, which could indicate eavesdropping. If there’s a high error rate, they abort the process.
Privacy Amplification:
If the key is deemed secure, they use algorithms to reduce any potential information leakage to an eavesdropper, further securing the key.
Advantages of Quantum Cryptography:
Unconditional Security: Based on the laws of physics, not on computational complexity, making it theoretically immune to advances in computing power.
Detection of Eavesdropping: Any attempt to measure or intercept the quantum key will change the quantum states, alerting the legitimate parties.
Challenges and Limitations:
Distance Limitation: Quantum signals degrade over distance due to decoherence, though this is being mitigated with quantum repeaters.
Speed: The key generation rate is currently slow compared to classical methods for wide use.
Implementation Issues: Real-world devices might not perfectly mimic quantum ideal behaviors, potentially opening vulnerabilities (side-channel attacks).
Cost and Complexity: QKD systems are expensive and complex to implement and maintain.
Practical Applications:
Secure Government Communications: For highly sensitive data transmission where absolute security is paramount.
Banking and Finance: For secure transaction keys.
Data Centers: For securing data at rest and in transit within a controlled environment.
Future Directions:
Quantum Internet: Extending quantum communication networks globally.
Quantum Random Number Generators: For true randomness in key generation.
Post-Quantum Cryptography: Developing classical cryptographic methods that are secure against quantum computers, complementing QKD.
Quantum cryptography represents a paradigm shift in secure communication, offering a layer of security that is fundamentally different from classical cryptography. However, its practical deployment faces technical and infrastructural challenges, and it’s often seen as a supplement to, rather than a replacement for, traditional cryptographic methods.





 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  Dogecoin
Dogecoin  Bitcoin Cash
Bitcoin Cash  Monero
Monero  Zcash
Zcash  Litecoin
Litecoin  PAX Gold
PAX Gold